Table of Contents
Understanding Microsoft Support Scams and Fake Virus Warnings
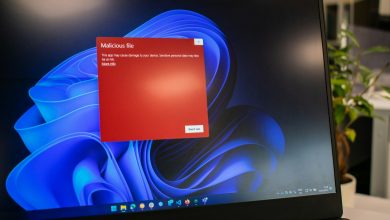
Microsoft support scams and fake virus warnings are deceitful tactics that cybercriminals use to exploit users. These scams often manifest in the form of alarming pop-up messages or unsolicited phone calls, claiming to be from Microsoft or other reputable tech companies. The primary objective is to trick the user into believing their computer is at risk due to a virus or other security threats. The scammers create a sense of urgency, compelling users to contact them through the provided numbers or links to resolve the supposed issues.
The methodology behind these scams can be elaborate, involving persuasive dialogues and the misuse of legitimate Windows utilities to convince the victim of non-existent problems. Victims may be coerced into purchasing unnecessary support services, granting remote access to their devices, or providing sensitive personal and financial information. Understanding the mechanics and motivations of these scams is crucial in safeguarding against them.
Identifying the Red Flags of a Fake Virus Alert
Recognizing the signs of a fake virus alert can significantly reduce the risk of falling victim to these scams. Such alerts often exhibit specific characteristics that, once identified, can be clear indicators of a scam attempt. Key red flags include:
- Unsolicited pop-up messages: Genuine Microsoft warnings do not appear as unsolicited pop-up ads within browsers, demanding immediate action.
- Messages requesting phone calls: Authentic error or warning messages from Microsoft and other tech entities will never include a phone number to call.
- Alarming language: Scammers use fear-inducing language to create a sense of urgency, claiming that immediate action is required to prevent data theft or damage.
- Inconsistencies and typos: Official messages from reputable companies will be professional in tone, free of spelling and grammatical errors that often plague scam attempts.
- Promises of easy fixes: Scammers may claim that complex issues can be resolved swiftly by their team, usually against a fee or by granting remote access to your device.
Identifying these red flags helps users differentiate between legitimate warnings and those intended to deceive.
How Scammers Use Fear Tactics in Microsoft Support Scams
In Microsoft support scams, cybercriminals masterfully employ fear tactics to manipulate their targets. These tactics hinge on the victim's fear of data loss, identity theft, and potential financial ruin. By presenting fabricated issues as imminent threats, scammers pressure users into making hasty decisions—such as paying for unnecessary services or permitting remote access to their computers. This modus operandi leverages the psychological impact of fear, exploiting the common desire to protect one's sensitive information and maintain system integrity.
Fear tactics can be particularly effective because they exploit the user's trust in the apparent source of the warning, often mimicking the visual design and language of official communications from Microsoft. The illusion of credibility and the simulated urgency combine to undermine the user's ability to critically evaluate the situation, increasing the likelihood of compliance with the scammer’s demands.
To counteract these tactics, it is vital to remain calm, skeptically assess the supposed threats, and rely on established procedures and contacts for resolving potential security issues. Recognizing the strategic exploitation of fear can empower users to confidently dismiss unfounded alerts and protect themselves from fraud.
Step-by-step Guide to Safely Remove Fake Virus Alerts
Eliminating fake virus alerts requires a methodical approach to ensure all traces of the adware or malware are removed without compromising your system's integrity. Follow these carefully structured steps to cleanse your computer and restore its performance.
Navigating Through Your Browser to Remove Unwanted Extensions
Adware and malware can often infiltrate systems through browser extensions. To tackle potential threats from this vector:
- Open your browser and access the extensions or add-ons menu.
- Review the list of installed extensions and identify any that appear unfamiliar or that were installed without your knowledge.
- Remove any suspicious extensions by clicking the remove or uninstall button next to the extension details.
This step helps rid your browser of any unwanted or potentially harmful extensions that could display fake virus alerts or redirect you to malicious sites.
Resetting Your Browser Settings to Default as a Precaution
If fake virus alerts persist even after cleaning your system and removing dubious extensions, resetting your browser to its default settings may be necessary. This action can help eliminate any remaining adware settings or changes made without your consent. The process for resetting varies among browsers but generally involves:
- Finding the advanced settings menu within your browser’s settings.
- Locating the option to reset the browser settings to their original defaults.
- Confirming the reset to initiate the process.
Resetting your browser should be treated as a last resort, as it will remove all customized settings, saved bookmarks, and stored passwords. Therefore, consider this step carefully and ensure you have backup copies of important data before proceeding.
Following these steps in order can help you efficiently and safely remove any fake virus alerts from your system, ensuring the security and optimal performance of your computer.
Protecting Your Identity: Tips and Best Practices
Identity theft is a pervasive issue in the digital age, compelling individuals to adopt stringent measures to safeguard their personal information. By implementing a combination of strong cybersecurity practices, you can significantly reduce the risk of identity theft. Below are essential tips and best practices to protect your identity online.
Creating Strong, Unique Passwords for Different Accounts
The foundation of personal cybersecurity is the creation of strong, unique passwords for each of your accounts. Here are some guidelines to enhance the strength and effectiveness of your passwords:
- Length and Complexity: Ensure your passwords are at least 12 characters long and include a mix of letters (both uppercase and lowercase), numbers, and special symbols.
- No Personal Information: Avoid using easily obtainable personal information such as birthdays, pet names, or family member names in your passwords.
- Use Phrases or Sentences: Consider using random phrases or sentences that are easy for you to remember but difficult for others to guess. Apply creative substitutions, e.g., replacing "o" with "0" or "a" with "@".
- Password Managers: Utilize a reputable password manager to securely store and manage your passwords. This tool can also assist in generating strong passwords and filling them automatically during logins, thereby reducing the risk of keylogging.
Adhering to these guidelines will fortify your online accounts against unauthorized access.
Regularly Updating Software and Operating Systems
Keeping your software and operating systems up to date is crucial in protecting your identity. Software developers regularly release updates and patches to address vulnerabilities that could be exploited by cybercriminals. To maintain optimum security:
- Enable Automatic Updates: Wherever possible, activate automatic updates for your operating system and applications to ensure you're always running the latest versions.
- Monitor for New Updates: Regularly check for updates on software that doesn't support automatic updating, and apply these updates as soon as they become available.
- Secure Your Web Browser: Use security extensions and regularly clear your browser's cache to protect against tracking and to mitigate the risk of malware infection through malicious websites.
By prioritizing regular updates, you protect your devices from known vulnerabilities and thereby secure your personal information.
Enabling Two-Factor Authentication Wherever Possible
Two-factor authentication (2FA) adds an extra layer of security to your online accounts, significantly enhancing your identity protection. 2FA requires not only a password and username but also something that only the user has on them, i.e., a piece of information only they should know or have immediately to hand - such as a physical token or a smartphone app-generated code. Adopt the following practices:
- Enable 2FA on all major accounts: Particularly on your email, banking, and social media accounts. Most platforms now offer some form of 2FA.
- Use Authenticator Apps: Whenever possible, opt for an authenticator app over SMS-based verification. Authenticator apps like Google Authenticator or Authy generate codes offline and are considered more secure than text message codes, which can be intercepted.
- Backup Codes: Securely store any backup codes provided during the 2FA setup process. These codes can be vital in case your 2FA method is temporarily unavailable.
Implementing two-factor authentication across your accounts drastically reduces the likelihood of unauthorized access, adding an essential protective barrier to your identity online.
When to Seek Professional Help: Recognizing Unsolvable Issues
While many tech problems can be resolved with a bit of research and elbow grease, there are certain scenarios where seeking professional help is not only advisable but necessary. Recognizing the signs that an issue is beyond your ability to solve can save you time, protect your data, and prevent further damage to your computer system. Here’s how to determine when it's time to call in the experts.
Recurring Malware or Virus Infections
If your computer continues to suffer from malware or virus infections despite your best efforts to clean it using reputable antivirus software, this may indicate a deeply embedded threat that requires specialized removal tools and expertise. Persistent or recurring infections can compromise your personal information and system integrity.
System Crashes and Unexplained Behavior
Frequent system crashes, blue screen errors, or unexplained computer behavior such as random restarts may signal underlying hardware issues or complex software conflicts. Professionals can run diagnostic tests to accurately identify and solve the root cause of such instability.
Data Loss and Hard Drive Failure
In the event of data loss or signs of hard drive failure, such as clicking noises or the inability to boot your operating system, seeking professional help is critical. Data recovery specialists have the tools and expertise necessary to potentially recover lost data and advise on data backup strategies to prevent future losses.
Network and Connectivity Issues
Chronic network and connectivity problems that persist after basic troubleshooting may indicate a more serious issue with your network configuration or hardware. Professional IT technicians can systematically isolate and resolve complex network problems, ensuring your connectivity is stable and secure.
When Security is Compromised
If you suspect that your computer’s security has been compromised, especially in cases of potential identity theft, financial fraud, or if your system has been hacked, it’s crucial to get professional help immediately. Cybersecurity experts can help contain the breach, remove any threats, and secure your system against future attacks.
In each of these scenarios, the common thread is the potential for significant data loss, compromised security, or irreparable harm to your computer system. Recognizing when you’re out of your depth and seeking professional help is not only a practical choice but also a necessary step in protecting your digital life.
Reporting Microsoft Support Scams and Fake Virus Warnings
It's crucial to report instances of Microsoft support scams and fake virus warnings to help safeguard not only your security but also to assist in the broader fight against cybercrime. When encountering such scams, your proactive steps in reporting them can contribute to the efforts to track down and penalize the perpetrators behind these fraudulent activities.
Authorities to Contact When You’ve Encountered a Scam
Upon recognizing a scam, knowing the correct authorities to contact is essential for an effective response. There are multiple platforms and organizations dedicated to combatting such deceitful practices:
- Microsoft Report a Scam Page: For scams impersonating Microsoft or involving its products, use the official Microsoft webpage dedicated to reporting scams (www.microsoft.com/reportascam). This platform allows users to report suspicious activities and support scam cases.
- Report Unsafe Websites in Microsoft Edge: If you encounter a suspicious site while using Microsoft Edge, you can report it directly through the browser. Navigate to Settings and More > Help and Feedback > Report unsafe site.
- Federal Trade Commission (FTC): For a broader approach, the FTC’s website (ReportFraud.ftc.gov) serves as a central reporting hub for scams, including tech support fraud. Reporting here contributes to the collective data that can lead to legal action against scammers.
- Local Law Enforcement: In cases where you've suffered financial loss or for immediate concerns, consider reporting the incident to your local law enforcement agency. They can provide direct assistance and advise on specific actions to take within your jurisdiction.
- Global Customer Service: For urgent assistance, particularly if scam involvement has led to security breaches or other immediate risks, contacting Microsoft’s global customer service can provide direct support and guidance on mitigating any damage.
By reporting scams through these channels, you play a significant part in the collective effort to clamp down on cybercriminal activities. Each report not only helps in potentially tracking down scammers but also aids in developing stronger protective measures for all users against future scams.